Thủ Thuật về What is an extended access-list? Mới Nhất
Lê Khánh Vy đang tìm kiếm từ khóa What is an extended access-list? được Update vào lúc : 2022-03-09 10:09:14 . Với phương châm chia sẻ Bí kíp về trong nội dung bài viết một cách Chi Tiết Mới Nhất. Nếu sau khi đọc tài liệu vẫn ko hiểu thì hoàn toàn có thể lại Comment ở cuối bài để Mình lý giải và hướng dẫn lại nha.
For those of you who are familiar with access control lists, you’re probably aware that there are many different types of access control lists. We have access control lists for IP version 4, for IP version 6, for IPX, for DECnet, for AppleTalk and the list goes on and on and on. What are you responsible for? We are responsible for IP version 4 this point, and that’s where our focus is, IP version 4. And we can break out IP version 4 access control lists into two different types, standard and extended. What’s the difference here?
- Standard ACL
- Checks ACL source address
Permits or denies entire protocol suite
Extended ACL
- Checks source and destination address
Generally permits or denies specific protocols and applications
- Source and destination TCP and UDP ports
Protocol type (IP, ICMP, UDP, TCP or protocol number)
Well it’s what parameters they look for and I want you to read standard, what does this standard look for here? What does it check? I want you to read that. And I am going to show a way to remember it. So you see standard does not look destination, which practically speaking, is not very useful. The lack of being able to look for a destination is quite limiting, you usually want to look for where it’s coming from and going to. But a standard access list has something in common with source address, doesn’t it? It’s the letter S, it is a great way to remember that standard access lists only look for source.
Extended access control lists, or extended ACLs, on the other hand, they’re far more powerful, they can look source and destination, they can look transport layer protocols such as TCP and User Data Protocol, or UDP. They can look application layer protocols over TCP and UDP, such as HTTP, FTP, Trivial File Transport Protocol, or TFTP, DNS, secure sockets layer, and secure shell. That sounds like a lot, so how do we remember that extended access lists can match for so much more than standard access control lists? Well when we were referring to our standard access control lists, we pointed out that it only checks the source address. Standard starts with S, source starts with S also.
So I remember it as standard, source only, S and S, whereas with extended, we have everything else. So the E helps us remember everything. Now there are certain things that we can’t match. We can’t match sequence numbers, acknowledgment numbers, we can’t match many of the flags in TCP for instance, we can match one of them and send bit. But it’s far more inclusive and so we are closer to everything. Bear in mind, when we enter these in, we have two sets of syntax, we have the old syntax and we have the new syntax. And we are going to expose you to both.
The old syntax is numbered, the new syntax is named, and the numbered syntax, it is kind of tricky. We don’t encounter numeric names all that often. In numbered standard access list, we have one through 99. There is an expanded range which we stay away from, there is no reason to use that anymore. The 1300 through 1999, we don’t use that, okay, steer clear. But one through 99 is standard, 100 through 199 is extended and the way to remember this range is they always end 99s, every single range ends 99 something. And when we extend to a three digit value, when we jump from two digits to three digits, we extend and therefore we get the extended IP access list range.
IPv4 ACL Type
Number Range / Identifier
Numbered Standard
1-99, 1300-1999
Numbered Extended
100-199, 2000-2699
Named (Standard and Extended)
Name
But that’s the syntax that quite frankly we’re more responsible for, but we’ve had for the better part of a decade now, named access control lists. In fact, it’s over a decade as we speak. What’s the benefit of a named access control list? Well named access control list, first of all, allows us to provide a descriptive name. So instead of our access control list being called 79 we can provide a descriptive name and that name can help us understand what the access control list is designed to accomplish. But what we really benefit from by using named access control lists is the ability to edit them, add and delete entries within that ACL.
You see, with numbered access control lists, if you need to add an entry, when you go to the command line interface and you want to add an entry, that will be looked before an entry that you already have in there. Now you just can’t go in there and just put in there, there is no way to do that with the syntax for creating that. So you’re limited on your editing ability, what do you have to do? Erase it all, re-create it. So Notepad comes in handy. All right, but with named access control list, we have the ability to go into the named access control list syntax, add, move, delete, change those entries in the access control list, as we see fit.
So much more powerful, the named access control list syntax. But don’t get us wrong here. The numbered access control list identification such as 1, 2, 3, 4 or 100 or 150, that is still the name of the access control list. And you’ll see it later, utilize named access control list syntax to edit a numbered access control list. It’s pretty cool and we will give you the ability to edit and to fix your mistakes with your numbered access control list without having to blow the whole thing away and remove it. So a really great syntax and you will learn it and you’ll love it and we will see it all, all the syntax as we progress through this course together.
Standard numbered ACLs
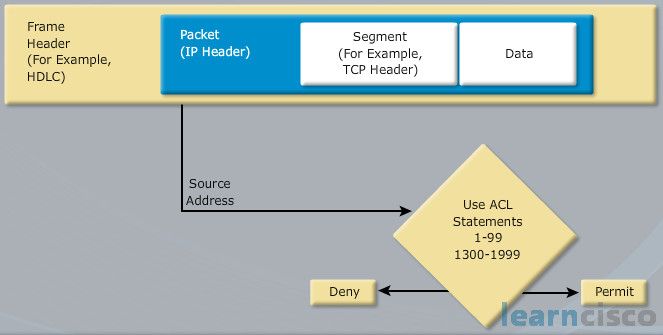
Standard access list, what do they look for? I am asking you, what do they look for? They look for the source parameter and here we can see that. So they are going to not worry about the layer 2 frame header, they are going to look the packet header, they are going to look the source field in the packet header and match based on that exclusively. So they are not going to go deeper into the transport layer. And none of these go into the data, okay. You would have to use some advanced firewall features to filter based on data.
Here is what we’ve been waiting for, the syntax, and it is not overly complicated, make note of that. It’s not overly complicated. First and foremost, we configure numbered access control lists in global configuration mode. We type in access-list and then we specify the access list number. So these are standard IPv4 access control lists, what are the number ranges? 1 to 99 and 1300 to 1999. When we specify any number out of those possible values, our router automatically knows that we are creating a standard IPv4 access control list and it will provide you with the correct syntax to use.
It won’t let you put in parameters that are not acceptable to the standard IP version 4 access control list. So you put in the wrong number, if you put in a 101, where you are trying to create a standard IP version 4 access control list, it will give you the syntax for an extended access control list, right? So be careful with your numbering, pick the right numbers and then you’ll specify which you want to happen to this traffic. Do you want to permit it? Do you want to deny it? You can also put a remark, what is a remark? It’s just a description. So you can describe this access control list, so when you review the access control list later, you will know what it’s for.
R1(config)#access-list 1 ?
deny Specify packets to reject
permit Specify packets to forward
remark Access list entry comment
R1(config)#access-list 1 permit ?
Hostname or A.B.C.D Address to match
host A single host address
R1(config)#access-list 1 permit 172.16.0.0 ?
/nn or A.B.C.D Wildcard bits
log Log matches against this entry
R1(config)#access-list 1 permit 172.16.0.0 0.0.255.255 ?
log Log matches against this entry
R1(config)#access-list 1 permit 172.16.0.0 0.0.255.255
Then we have our source, what is the source? Remember, earlier when we were looking addresses and wildcard mask combinations… Well the source is the source address, that starting point that we want to use for that range comparison. So if we look our example, we have 172.16.0.0 as the address, the source and then mask. What is the mask? Be careful here, it is not, I repeat, it’s not the subnet mask. It is the wildcard mask. This is where we put in the wildcard mask. So in our example 0.0.255.255, so what is the range of addresses that this access control list, that we just crafted, is going to check? 172.16.0.0 through 172.16.255.255.
So you see how important that wildcard mask is, and understanding what it does, it’ll help you craft them and read them. It says here that there’s a default wildcard mask, take that with a grain of salt, your operating system generally speaking will not accept the syntax anymore when you put in any entry inside of your access control list that lacks a wildcard mask. Okay, so that’s old behavior and not representative of anything that’s recent. When we put in an entry such as what we see in global configuration mode with access-list, that’s just one entry. Bear in mind, if we wanted to add another entry, we would still have access-list 1 and then we will build the next permit or deny sequence. access-list 1 again, access-list 1 again, if we want to build a larger and larger access control list. What’s the minimum size of an access control list?
A minimum size would be one permit statement. Yeah I guess there can’t just be one deny statement, that would be useless, unless you’re logging, but that wouldn’t let anything through. And the maximum is whatever you can dream up and whatever you have the endurance for. Once you perfect your access control list in global configuration mode as we see here, you can validate it. But to show access lists, command and that would in fact show all access lists, IPv4, IPv6, Mac address access list, IPX, AppleTalk, but usually we just have IPv4 and may be nowadays some IPv6.
Standard IP access list 1
10 permit 172.16.0.0, wildcard bits 0.0.255.255
And we can see the one entry. Now wait a minute, wait a minute, we put in permit 172.16 with that wildcard mask, what’s the 10 there? What is that 10 that just sprung to life inside of our access list? The 10 is an automatic sequence number that is added to the access list. It will be 10 by default. If we were to create another entry…so we type in access-list 1 permit 192.168.1.0 0.0.0.255, it would be automatically provided a sequence number. And it would be 20, the next one in the list and the next one will be 30 and 40 and 50, it’s how we keep track of them, the sequence number, the order we created them in.
And this is important, remember how we said, if we want to edit the access control list, we might want to add an entry here and there, but we can only do that with named syntax, we are unable to do that here with this standard numbering syntax, but those sequence numbers will be the defining factor of where our entry goes. If we add or move or delete or change and we will see that later on, we will see that later on only when we enter into the named access control list syntax of how these sequence numbers can be used and manipulated to our advantage.
Removing an access list is very easy, remember that powerful no command, type in no access-list and then the number of the access list you want to remove. Be careful, be careful. Let’s say you typed in no access-list 1 permit 172.16.0.0 0.0.255.255. So you want to remove a standard access list entry you created earlier. You type in no and you specify the whole command that you typed in before, will that remove just that one entry? I will repeat that, will that remove just the one entry? At first thought, yeah, that’s first thought, but if you try that and you tested it? No, that is not what will happen. It won’t remove just that one entry, what will it do? It will get rid of the whole thing, so some of you out there have had exposure to this. It is really bizarre behavior in the IOS.
R1#config t
Enter configuration commands, one per line. End with CNTL/Z.
R1(config)#no access-list 1
R1(config)#end
R1#sh access-lists
R1#

Video What is an extended access-list? ?
Bạn vừa đọc tài liệu Với Một số hướng dẫn một cách rõ ràng hơn về Clip What is an extended access-list? tiên tiến nhất
Share Link Down What is an extended access-list? miễn phí
You đang tìm một số trong những Share Link Down What is an extended access-list? Free.
Hỏi đáp thắc mắc về What is an extended access-list?
Nếu sau khi đọc nội dung bài viết What is an extended access-list? vẫn chưa hiểu thì hoàn toàn có thể lại Comments ở cuối bài để Tác giả lý giải và hướng dẫn lại nha
#extended #accesslist – 2022-03-09 10:09:14