Kinh Nghiệm về What is a technical control that inspects a network incoming and outgoing traffic and either blocks or permits it according to rules the organization ... 2022
Bùi Lam Khê đang tìm kiếm từ khóa What is a technical control that inspects a network incoming and outgoing traffic and either blocks or permits it according to rules the organization ... được Cập Nhật vào lúc : 2022-09-21 03:14:05 . Với phương châm chia sẻ Bí quyết Hướng dẫn trong nội dung bài viết một cách Chi Tiết Mới Nhất. Nếu sau khi tham khảo nội dung bài viết vẫn ko hiểu thì hoàn toàn có thể lại Comments ở cuối bài để Mình lý giải và hướng dẫn lại nha.A firewall is a network security device that monitors incoming and outgoing network traffic and decides whether to allow or block specific traffic based on a defined set of security rules.
Nội dung chính- What type of firewall inspects network traffic a higher level in the OSI model than a traditional stateful packet inspection firewall does?What lists out and rates the vulnerabilities of an organization?What feature does a firewall provide?Is the art of manipulating people into breaking normal security procedures or divulging confidential information?
Firewalls have been a first line of defense in network security for over 25 years. They establish a barrier between secured and controlled internal networks that can be trusted and untrusted outside networks, such as the Internet.
A firewall can be hardware, software, software-as-a service (SaaS), public cloud, or private cloud (virtual).
A firewall is a network security device, either hardware or software-based, which monitors all incoming and outgoing traffic and based on a defined set of security rules it accepts, rejects or drops that specific traffic.
Accept : allow the traffic
Reject : block the traffic but reply with an “unreachable error”
Drop : block the traffic with no reply
A firewall establishes a barrier between secured internal networks and outside untrusted network, such as the Internet.
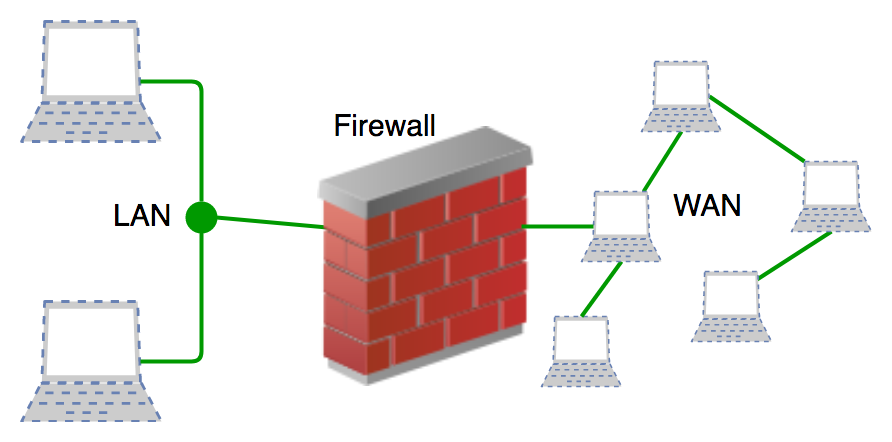
History and Need for Firewall
Before Firewalls, network security was performed by Access Control Lists (ACLs) residing on routers. ACLs are rules that determine whether network access should be granted or denied to specific IP address.
But ACLs cannot determine the nature
of the packet it is blocking. Also, ACL alone does not have the capacity to keep threats out of the network. Hence, the Firewall was introduced.
Connectivity to the Internet is no longer optional for organizations. However, accessing the Internet provides benefits to the organization; it also enables the outside world to interact with the internal network of the organization. This creates a threat to the organization. In order to secure the internal network from unauthorized traffic, we need a Firewall.
How Firewall Works
Firewall match the network traffic against the rule set defined in its table. Once the rule is matched, associate action is applied to the network traffic. For example, Rules are defined as any employee from HR department cannot access the data from code server and the same time another rule is defined like system administrator can access the data from both HR and technical department. Rules can be defined on the firewall based
on the necessity and security policies of the organization.
From the perspective of a server, network traffic can be either outgoing or incoming. Firewall maintains a distinct set of rules for both the cases. Mostly the outgoing traffic, originated from the server itself, allowed to pass. Still, setting a rule on outgoing traffic is always better in order to achieve more security and prevent unwanted communication.
Incoming traffic is treated differently. Most traffic which reaches on the
firewall is one of these three major Transport Layer protocols- TCP, UDP or ICMP. All these types have a source address and destination address. Also, TCP and UDP have port numbers. ICMP uses type code instead of port number which identifies purpose of that packet.
Default policy: It is very difficult to explicitly cover every possible rule on the firewall. For this reason, the firewall must always have a default policy. Default policy only consists of action
(accept, reject or drop).
Suppose no rule is defined about SSH connection to the server on the firewall. So, it will follow the default policy. If default policy on the firewall is set to accept, then any computer outside of your office can establish an SSH connection to the server. Therefore, setting default policy as drop (or reject) is always a good practice.
Generation of Firewall
Firewalls can be categorized based on its generation.
First Generation- Packet Filtering Firewall : Packet filtering firewall is used to control network access by monitoring outgoing and incoming packet and allowing them to pass or stop based on source and destination IP address, protocols and ports. It analyses traffic the transport protocol layer (but mainly uses first 3 layers).Packet firewalls treat each packet in isolation. They have no ability to tell whether a packet is part of an existing stream of traffic. Only It can allow or deny the packets based on unique packet headers.
Packet filtering firewall maintains a filtering table which decides whether the packet will be forwarded or discarded. From the given filtering table, the packets will be Filtered according to following rules:
 Incoming packets from network 192.168.21.0 are blocked.Incoming
packets destined for internal TELNET server (port 23) are blocked.Incoming packets destined for host 192.168.21.3 are blocked.All well-known services to the network 192.168.21.0 are allowed.Second Generation- Stateful Inspection Firewall : Stateful firewalls (performs Stateful Packet Inspection) are able to determine the connection state of packet, unlike Packet filtering firewall, which makes it more efficient. It keeps track of the
state of networks connection travelling across it, such as TCP streams. So the filtering decisions would not only be based on defined rules, but also on packet’s history in the state table.Third Generation- Application Layer Firewall : Application layer firewall can inspect and filter the packets on any OSI layer, up to the application layer. It has the ability to block specific content, also recognize when certain application and protocols (like HTTP, FTP) are
being misused.
Incoming packets from network 192.168.21.0 are blocked.Incoming
packets destined for internal TELNET server (port 23) are blocked.Incoming packets destined for host 192.168.21.3 are blocked.All well-known services to the network 192.168.21.0 are allowed.Second Generation- Stateful Inspection Firewall : Stateful firewalls (performs Stateful Packet Inspection) are able to determine the connection state of packet, unlike Packet filtering firewall, which makes it more efficient. It keeps track of the
state of networks connection travelling across it, such as TCP streams. So the filtering decisions would not only be based on defined rules, but also on packet’s history in the state table.Third Generation- Application Layer Firewall : Application layer firewall can inspect and filter the packets on any OSI layer, up to the application layer. It has the ability to block specific content, also recognize when certain application and protocols (like HTTP, FTP) are
being misused.In other words, Application layer firewalls are hosts that run proxy servers. A proxy firewall prevents the direct connection between either side of the firewall, each packet has to pass through the proxy. It can allow or block the traffic based on predefined rules.
Note: Application layer firewalls can also be used as Network Address Translator(NAT).
Next Generation Firewalls (NGFW) : Next Generation Firewalls are being deployed these days to stop modern security breaches like advance malware attacks and application-layer attacks. NGFW consists of Deep Packet Inspection, Application Inspection, SSL/SSH inspection and many functionalities to protect the network from these modern threats.Types of Firewall
Firewalls are generally of two types: Host-based and Network-based.
Host- based Firewalls : Host-based firewall is installed on each network node which controls each incoming and outgoing packet. It is a software application or suite of applications, comes as a part of the operating system. Host-based firewalls are needed because network firewalls cannot provide protection inside a trusted network. Host firewall protects each host from attacks and unauthorized access.Network-based Firewalls : Network firewall function on network level. In other words, these firewalls filter all incoming and outgoing traffic across the network. It protects the internal network by filtering the traffic using rules defined on the firewall. A Network firewall might have two or more network interface cards (NICs). A network-based firewall is usually a dedicated system with proprietary software installed.Both types of firewall have their own advantages.
References:
https://en.wikipedia.org/wiki/Firewall_(computing)
https://www.cisco.com/c/en_in/products/security/firewalls/what-is-a-firewall.html
://nptel.ac.in/courses/106105084/31
This article is contributed by Abhishek Agrawal. Please write comments if you find anything incorrect, or you want to share more information about the topic discussed above.
What type of firewall inspects network traffic a higher level in the OSI model than a traditional stateful packet inspection firewall does?
A proxy firewall (aka application-level gateway) inspects packets the application layer of the Open Systems Interconnection (OSI) reference model.What lists out and rates the vulnerabilities of an organization?
The risk matrix lists the vulnerabilities in a table, and managers rate the level of risk each one presents in areas such as confidentiality, company reputation, finances, system availability, and operations.What feature does a firewall provide?
A firewall can help protect your computer and data by managing your network traffic. It does this by blocking unsolicited and unwanted incoming network traffic. A firewall validates access by assessing this incoming traffic for anything malicious like hackers and malware that could infect your computer.Is the art of manipulating people into breaking normal security procedures or divulging confidential information?
What is social engineering? Social engineering is an attack vector that relies heavily on human interaction and often involves manipulating people into breaking normal security procedures and best practices to gain unauthorized access to systems, networks or physical locations or for financial gain. Tải thêm tài liệu liên quan đến nội dung bài viết What is a technical control that inspects a network incoming and outgoing traffic and either blocks or permits it according to rules the organization establishes?